social media
The tech industry makes the social media world go 'round; explore the technologies that keep us all connected.
The Viral Wave of December 2025.. AI-Generated.
The digital world never sleeps, and December 2025 is proving to be one of the most electrifying months for viral content, cultural phenomena, and internet-breaking moments. From AI-powered nostalgia trips to unexpected food obsessions and social media trends that are reshaping how we communicate online, here's everything you need to know about what's trending right now.
By Punit kumar2 months ago in 01
How to Hack a Snapchat Account: Techniques, Tools, and Protection. AI-Generated.
Snapchat, with its ephemeral messages and close-knit social circles, holds a trove of private conversations and sensitive media. This has made it a prime target for individuals looking to gain unauthorized access. This article provides a deep dive into the world of Snapchat account hacking, exploring the techniques used by attackers, the tools they employ, and, most importantly, how you can protect yourself. We will also cover the legal and ethical implications of such actions.
By Alexander Hoffmann2 months ago in 01
The Complete Guide to Instagram Account Hacking 2026: Threats, Methods, and Comprehensive Protection Strategies. AI-Generated.
The Growing Threat to Instagram Security Instagram has evolved from a simple photo-sharing app to a central hub for personal expression, business marketing, and social connection. With over 2 billion active monthly users, the platform has become a prime target for cybercriminals. Account hacking represents a significant threat that can lead to identity theft, financial loss, reputational damage, and emotional distress. This comprehensive guide examines the methods attackers use, the tools involved, and most importantly, provides actionable protection strategies to safeguard your digital identity.
By Alexander Hoffmann2 months ago in 01
How Professional Carpet Cleaning Improves Office Hygiene
A healthier and friendlier workplace is supported by clean office carpets. Frequent care is also a way of keeping up with a professional image. One clever solution is regular maintenance that is backed by professional office carpet cleaning.
By Nikki James2 months ago in 01
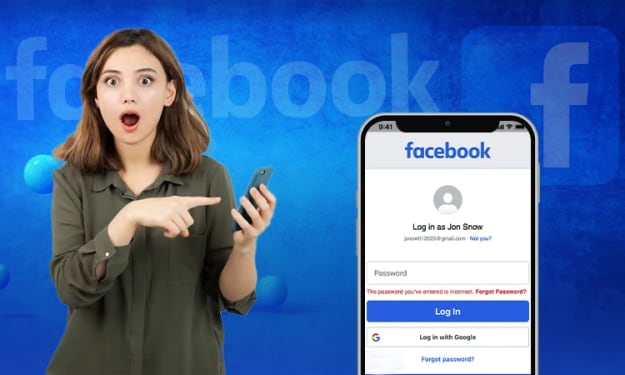
The Complete Guide to Hack Facebook: Understanding Hacking Methods and Protection Strategies. AI-Generated.
Facebook account security is more critical than ever. With over 2.9 billion monthly active users, Facebook accounts are prime targets for cybercriminals. This comprehensive guide explores the various methods used to compromise Facebook accounts, legitimate protection strategies, and recovery procedures—all while maintaining ethical boundaries and legal compliance.
By Alexander Hoffmann2 months ago in 01
Inside Liam Gordon Murphy’s Method for Strategic Alignment and Results
In today’s fast-moving business environment, leaders are expected to make confident decisions amid constant pressure. Markets shift, teams evolve, and competition intensifies. In this landscape, success is no longer defined by speed alone—it is defined by alignment. Leaders who grow sustainably are those who bring structure, clarity, and calm into complexity.
By Jeffrey D. Gross MD2 months ago in 01
Mark Fagan’s Cardenden Perspective on Memory and Nature
Stories are often shaped by where they begin. For Mark Fagan, that beginning lies in Cardenden, a village in Fife where landscape, history, and everyday life quietly inform the imagination. His writing does not separate people from place. Instead, it explores how memory and nature grow together, shaping identity over time.
By Jeffrey D. Gross MD2 months ago in 01
How Experienced Leader Gautham Chindambram Drives Modern Cannabis Growth
In the competitive and fast-evolving cannabis landscape, strong leadership and operational clarity are essential for sustainable success. As the driving force behind Passion Farms, Gautham Chindambram has played a central role in building a nationally recognized brand rooted in quality, efficiency, and strategic foresight. His approach reflects a balance of hands-on cultivation knowledge, disciplined supply chain management, and a clear understanding of multi-state market dynamics. Rather than relying on rapid expansion alone, his leadership emphasizes consistency, compliance, and long-term value creation.
By Gautham Chidambaram2 months ago in 01
Advanced IT Infrastructure Design for Secure and Reliable Operations
Modern organizations depend on IT infrastructure that is not only powerful, but also secure, reliable, and adaptable. Downtime, security breaches, and poorly designed systems can disrupt operations, damage trust, and increase costs. Advanced infrastructure design focuses on preventing these risks while enabling long-term growth. Professionals like Shane Yoder exemplify how experience-driven design decisions create technology environments that perform consistently under pressure.
By Jeffrey D. Gross MD2 months ago in 01
The Anatomy of TikTok Hacking: Techniques Used by Cybercriminals and How to Fortify Your Account. AI-Generated.
In the dynamic world of social media, TikTok has emerged as a cultural phenomenon, boasting over a billion active users worldwide. This massive reach, combined with the platform's integration of personal data, creative content, and sometimes financial transactions, has made it an attractive target for cybercriminals. This article delves into the sophisticated methods hackers employ to compromise TikTok accounts, demystifies their techniques, and provides a comprehensive guide to protecting your digital presence. Understanding these threats is the first step toward building an effective defense.
By Alexander Hoffmann2 months ago in 01