Common Cloud Security Threats: Your 2026 Protection Guide
Discover the common cloud security threats organizations face in 2026. Learn to identify and mitigate risks like data breaches, misconfigurations, and API vulnerabilities. Explore our guide for protection.

Why You Are Still Getting Hacked in 2026
You would think by now we would have this cloud thing figured out. I reckon it is almost funny. We have got flying taxis in some cities and AI that can write poetry, but we still leave our databases wide open. Real talk, the common cloud security threats we face today are often just updated versions of the same old mistakes.
It is proper dodgy how often companies forget the basics. You spend millions on fancy tools but forget to lock the back door. I have seen it heaps of times. A small firm thinks they are safe because they are too small to notice. That is all hat and no cattle, mate. Hackers do not care about your size, only your data.
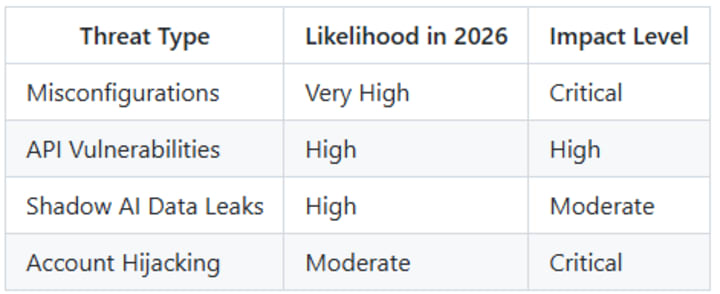
The Misconfiguration Nightmare
Get this. Most cloud failures are still your fault. Not the provider. Not AWS or Azure. You. Gartner has been saying for years that nearly all cloud security failures through 2025 and 2026 would be the customer's responsibility. It is usually just a tick box left unchecked.
I once saw a dev leave an S3 bucket public because it was easier for testing. He forgot to change it back. By the next arvo, half their customer list was on a dark web forum. It is hella frustrating because it is so preventable. Misconfigurations are the low-hanging fruit for any script kiddie with a scanner.
The Shadow AI Problem
Everyone is stoked about AI. But thing is, your employees are using unsanctioned AI tools to process company data. This is the new shadow IT. If someone uploads a confidential strategy doc to a random LLM to summarize it, that data is gone. You no longer control it.
Teams working in this space, like those at mobile app development company california, see this shift daily. They understand that every new feature is a potential new entry point. If you are not watching what your staff are fixin' to do with AI, you are already behind the curve. It is a massive headache for CISOs everywhere.
Common Cloud Security Threats: The Heavy Hitters
The landscape has shifted. We are not just worried about a simple virus anymore. We are talking about sophisticated, multi-stage attacks that move faster than a Texas thunderstorm. You have to be right every time. The hacker only has to be right once. Fair dinkum, those odds suck.
Data breaches in 2026 are costing more than ever. The IBM Cost of a Data Breach Report notes that the average cost has climbed toward $5 million. That is enough to sink a mid-sized business. If you are not taking this seriously, you are playing with fire.
API Vulnerabilities Are The New Front Door
APIs are everywhere. They are the glue that holds your mobile apps and cloud services together. But they are often built in a rush. A dodgy API is like a key left under the mat. Hackers love them because they often bypass traditional firewalls.
Salt Security has highlighted that API attack traffic is growing way faster than regular traffic. It is a proper mess. If your mobile app development team is not prioritizing API security, they are essentially building a house without a front door. You need to validate every single request.
Account Hijacking and MFA Fatigue
Think MFA makes you safe? Think again. In 2026, hackers use MFA fatigue. They spam your phone with requests until you hit "approve" just to make it stop. Or they use sophisticated session hijacking to steal your login tokens. It is sneaky stuff.
I have been there. It is 3 AM and your phone starts buzzing. You are tired and just want to go back to sleep. One wrong tap and the keys to the kingdom are gone. This is why passwordless authentication is becoming the standard. It is just safer.
"The shift to cloud-native environments has expanded the attack surface exponentially, making identity the new perimeter." — Gil Shwed, Founder and CEO of Check Point Software
Insecure Third-Party Integrations
You are only as strong as your weakest link. Usually, that link is a third-party plugin or service you integrated three years ago and forgot about. These supply chain attacks are hella dangerous because you trust the source. But if the source gets popped, you are next.
It is like a bad relationship. You think everything is fine until you find out they have been sharing your secrets with everyone in town. You need to audit your permissions. Don't give a calendar app access to your entire database. That is just asking for trouble, y'all.
The Human Element: Why We Are the Problem
I reckon humans are the biggest bug in any system. You can have the best encryption in the world, but if Bob from accounting clicks a link for a "free coffee voucher," it is game over. Phishing has become terrifyingly realistic thanks to AI. No more "Dear Valued Customer" with bad spelling.
Now, it is a voice note from your boss that sounds exactly like him. Or a video call that looks perfect. Deepfakes are no longer just for Hollywood. They are a core part of the common cloud security threats playbook in 2026. It is enough to make you want to go back to pen and paper.
Social Engineering 2.0
Social engineering is fixin' to get a lot worse. Hackers use social media to build a profile of you. They know where you went on holiday and what your dog is named. They use this to build trust. It is not just a random email anymore. It is a conversation.
I once nearly fell for one myself. It was a message about a package I was actually expecting. The timing was perfect. I only stopped because the URL looked a bit dodgy. Always check the URL, mate. It is the oldest trick in the book, but it still works.
The Insider Threat
Not everyone inside your company is your friend. Sometimes it is a disgruntled employee. Other times, it is just someone being careless. Insider threats are hard to spot because they already have the keys. They do not need to break in.
💡 Kevin Mandia (@kevinmandia): "Cloud security isn't just about keeping people out; it's about monitoring those who are already in." — Mandiant Insights
You need to implement Zero Trust. Do not trust anyone by default. Verify everything. It sounds cynical, but in 2026, it is the only way to stay sane. If a developer is suddenly downloading the entire customer database at midnight, you should probably know about it.
Ransomware in the Cloud
Ransomware has evolved. It is no longer just about locking your files. Now, they steal the data first and threaten to leak it. They call it double extortion. If you do not pay, your secrets go public. Even if you have backups, you are still in a bind.
Cloud-based ransomware is fast. It can encrypt thousands of files in seconds. By the time your admin gets the alert, the damage is done. This is why real-time detection is no longer optional. You need tools that can kill a process the second it looks suspicious.
Future Trends: What Is Coming Next
Looking toward 2027, the battle is moving to the edge. As more processing happens on local devices rather than central servers, the attack surface will grow again. We are also fixin' to see the rise of quantum-resistant cryptography. Current encryption might not hold up against quantum computers for much longer. Market data from MarketsandMarkets suggests the cloud security sector will hit over $100 billion by 2028 as companies scramble to keep up. We will see more autonomous defense systems where AI fights AI in real-time. It is going to be a wild ride, and if you are not prepared, you will be left in the dust.
Autonomous Security Operations
We cannot keep up with the speed of attacks manually. We need machines to fight machines. In 2026, SOC teams are using AI to triage thousands of alerts. This helps them focus on the real threats rather than the noise. It is hella efficient when it works.
But wait, there is a catch. The hackers are using the same AI to find vulnerabilities. It is an arms race. Every time we build a better shield, they build a better sword. You have to keep updating your stack or you will get sorted out real quick.
The Death of the Perimeter
The idea of a "secure network" is dead. Everyone is working from everywhere. Your office is a coffee shop, a home office, or a beach in Bali. This means your security must follow the user, not the building. SASE (Secure Access Service Edge) is no longer a buzzword; it is a necessity.
I reckon this is a good thing. It forces us to be more disciplined. We can't rely on a physical firewall anymore. Every device has to be its own fortress. It is more work, but it is a much more robust way to handle the common cloud security threats of the modern era.
"In the cloud, security is a continuous process, not a destination. If you stop moving, you're a target." — Dr. Zero Trust (Chase Cunningham), Forrester Research Analysis
💡 Security Awareness (@SecAwareness): "Your most expensive security tool is useless if your team doesn't know how to spot a dodgy link. Invest in people, not just software." — Infosecurity Magazine
Serverless Security Risks
Serverless is great for developers. You just write code and it runs. But it is a nightmare for security. Traditional tools cannot see inside a serverless function. If a function is hijacked, it can be used to scan your internal network or mine crypto on your dime.
It is like having a ghost in the machine. You know something is wrong, but you can't see where it is coming from. You need specialized tools that can monitor these ephemeral environments. Do not assume because there is "no server" that there is "no risk." That is a rookie mistake.
Wrapping Up the Chaos
Staying safe in the cloud in 2026 is a full-time job. It is not something you set and forget. You have to be proactive. Audit your configs. Secure your APIs. Train your people. It is a lot of effort, but it is cheaper than a breach. No cap.
Real talk, most of the common cloud security threats are still preventable. We just need to stop being lazy. Lock your buckets, rotate your keys, and for the love of all things holy, stop clicking on random links. It is not rocket science, it is just common sense. Stay safe out there, y'all.






Comments
There are no comments for this story
Be the first to respond and start the conversation.